Which of the Following Statements Best Describes Nist
Examples of diploblastic species include jellyfish comb jellies corals and sea anemones. Question 4 of 10 100 Points Which of the following UC applications can eliminate the need for face-to-face training.
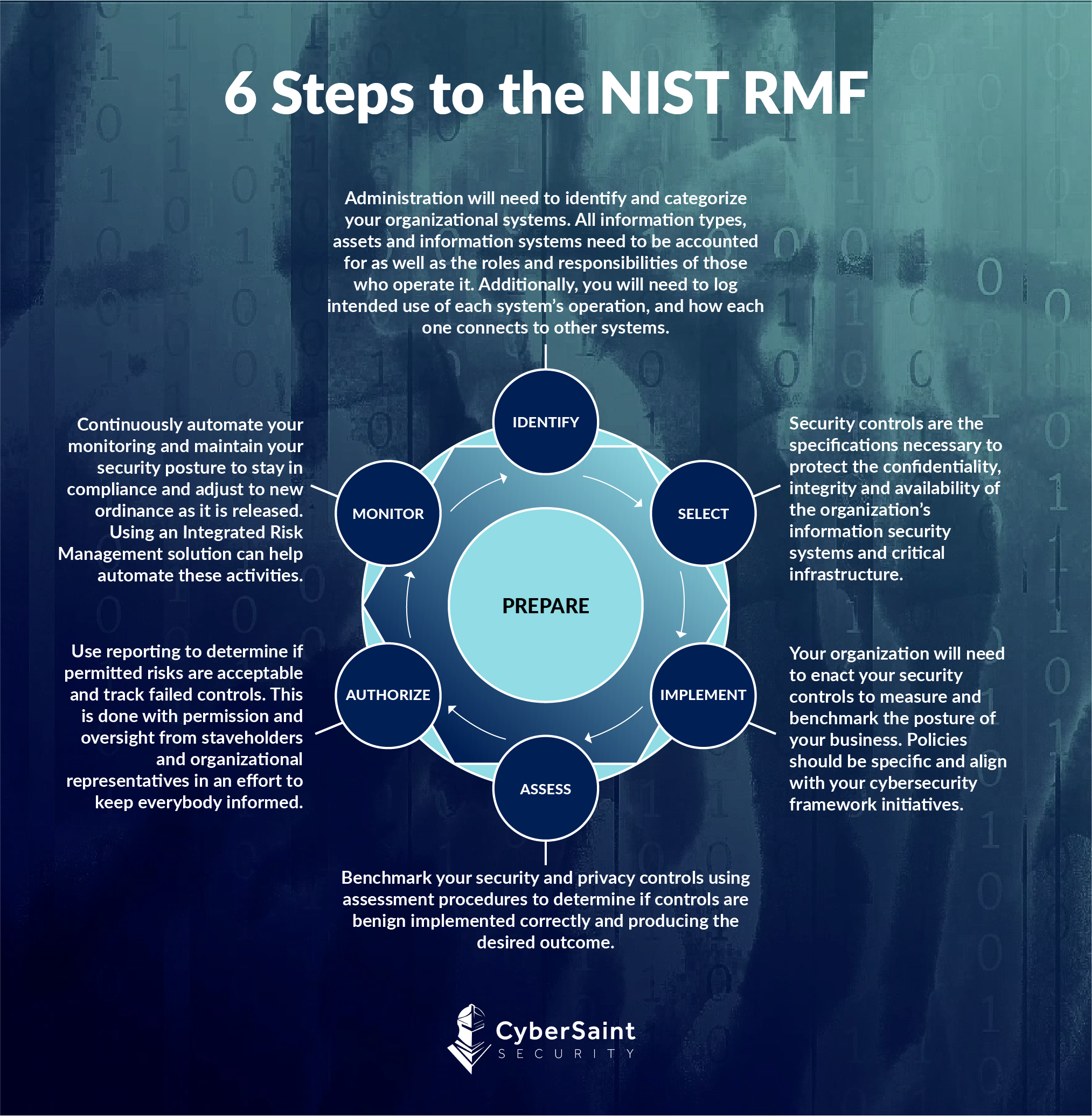
Infographic The Six Steps Of The Nist Risk Management Framework Rmf
If the population standard deviation increases the confidence intervaldecreases in width.

. These sample questions help you to obtain a remarkable progress in your AZ-900 exam preparation. Risk refers to the chance that an outcome or investments actual gains will differ from an. 212-Which of the following term best describes a weakness that could potentially be exploited.
Is no longer acceptable at some point in the future and include this migration plan in its digital identity acceptance statement. It is the possible risk after implementing all security measures. AZ-900 exam tests the skills of candidates such as Cloud concepts Azure services Azure workloads Azure security privacy and Azure pricing support.
It is an indicator of threats coupled with vulnerability. Which of the following statements about confidence interval is correct. By having basic knowledge of cloud services and Microsoft Azure anyone can take this exam.
NIST develops cybersecurity standards guidelines best practices and other resources to meet the needs of US. Which NIST incident response life cycle phase includes continuous monitoring by the CSIRT to quickly identify and validate an. Which of the following statements best describes strategic risk.
In which of the IT domains is a hub considered a major component of risk. NIST Risk Management Framework 5 Three Levels of Organization -Wide Risk Management. Managing Information Security Risk Organization Mission and Information System View Multi-level risk management approach Implemented by the Risk Executive Function Enterprise Architecture and SDLC Focus Supports all steps in the RMF.
The Core includes five high level functions. How does risk management impact an organization. Affects the survivability 4.
Which of the following statements best describes risk. The probability of loss of a valued resource. AAn external situation or event with the potential to cause harm to an IT system BA negative effect or influence on an information system CThe probability of loss of a valued resource DAn error or weakness in the security system.
The probability of loss of a valued resource 2. Uses a local scripting engine. NIST SP 800-39.
Examples of triploblastic animals include platyhelminthes annelids arthropods molluscs echinoderms and chordates. Unknown NOT USER DOMAIN LAN DOMAIN 3. If the sample size is fixed the confidence interval gets wider as we increase the confidence the confidence coefficient.
Concerning residual risk which of the following statements is true. The Framework Core is designed to be intuitive and to act as a translation layer to enable communication between multi-disciplinary teams by using simplistic and non-technical language. Question 10 25 25 points Which of the following describes the best known defense to protocol issues.
Which meta-feature element in the Diamond Model describes tools and information such as software black hat knowledge base username and password that the adversary uses for the intrusion event. Make a list of all equipment software and data you use including laptops smartphones tablets and point-of-sale devices. A users PC is infected with a virus that appears to be a memory resident and loads anytime an external universal serial bus USB thumb drive is attached.
Question 5 of 10 100 Points SIP is more secure than VoIP. Which of the following statement best describes the principle of Division of Work a Work should be divided into small tasks b Labour should be divided c Resources should be divided among jobs d It leads to specialisation. Functions Categories and Subcategories.
A chunk of data or sequence of commands that take advantage of a bug glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software. Our activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in technologies and. The Core consists of three parts.
NIST Special Publication 800-63B. Written to the partition table of a disk. Industry federal agencies and the broader public.
Ensuring that the most current software version and patches are used Using only one type of operating system Making sure all the hardware is the newest version available Validating all input on the system. A Risk that relates to monetary loss B Risk that relates to adverse business decisions C Risk that relates to loss resulting from inadequate or failed processes or systems D Risk that relates to violations of laws rules regulations or policy. It is a weakness or lack of control that can be exploited by a risk.
Section 101 the following sections describe other usability considerations specific to particular. You can put the NIST Cybersecurity Framework to work in your business in these five areas. Identify Protect Detect Respond and.
6 Authenticator Lifecycle Management. It is the possible risk prior to implementing all security measures. What are diploblastic animals give examples.
SP 800-63 Digital Identity Guidelines This document SP 800-63 provides an overview of general identity frameworks using authenticators credentials and assertions together in a digital system and a risk-based process of selecting assurance levels. 213-Which of the following best describes an exploit. Create and share a company cybersecurity policy that covers.
SP 800-63 contains both normative and informative material. Examine the following options and determine which describes the infection type. EVideo conferencing Answer Key.
Identify Protect Detect Respond and Recover.
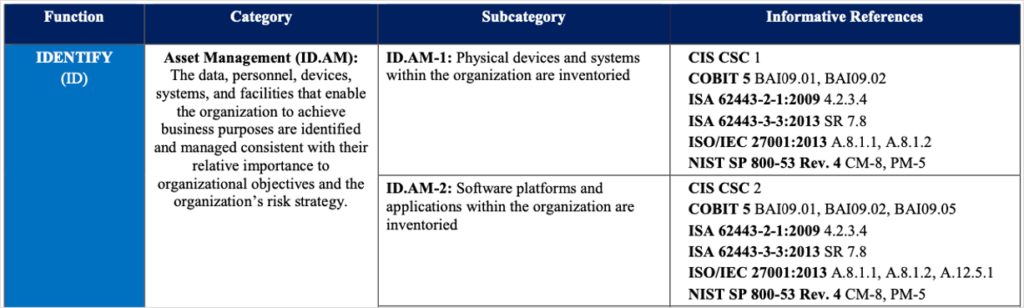
Everything To Know About Nist Csf Informative References Axio

Nist Cybersecurity Implementation Tiers In Plain English
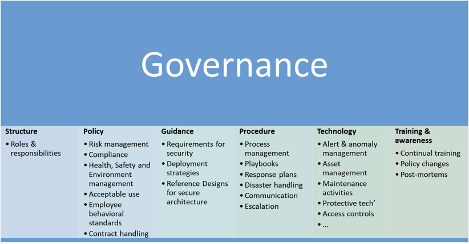
Mitre Att Ck Vs Nist Csf Verve Industrial

Vision Statement Examples For Business Vision Statement Examples Mission Statement Examples Business Mission Statement Examples
0 Response to "Which of the Following Statements Best Describes Nist"
Post a Comment